Security vulnerability scanning is a term used to identify known vulnerabilities in a software package. Just like in legacy systems, we also need to regularly perform vulnerability scans in the container world.
In container architecture, we package our products into images and distribute them to environments or use images that have already been distributed. Performing image scans before deploying a container image to an environment or using a pre-existing image in our environment allows us to identify vulnerable packages within the container image. Therefore, image scanning is one of the most important components of the DevSecOps concept.
There are multiple options for performing image scans, and one of them is a tool called Trivy, developed by Aqua Security as an open-source tool.
Trivy is an image scanning tool that reports security vulnerabilities in container images.
Installing Trivy is quite simple, and there is installation support for multiple operating systems. In this blog, we will share the installation process for the Ubuntu operating system. You can complete the installation by following the steps below.
sudo apt-get install wget apt-transport-https gnupg lsb-release
wget -qO - https://aquasecurity.github.io/trivy-repo/deb/public.key | sudo apt-key add -
echo deb https://aquasecurity.github.io/trivy-repo/deb $(lsb_release -sc) main | sudo tee -a /etc/apt/sources.list.d/trivy.list
sudo apt-get update
sudo apt-get install trivyYou need to use a tool like Docker or Podman on the server where you will perform the scan to download images.
Once you have completed the Trivy installation, you can open the command line and perform an image scan as shown below.
trivy image httpd:latest
When the image scan is complete, Trivy will provide a report. This report lists the details of the vulnerable packages inside the container in a table format.
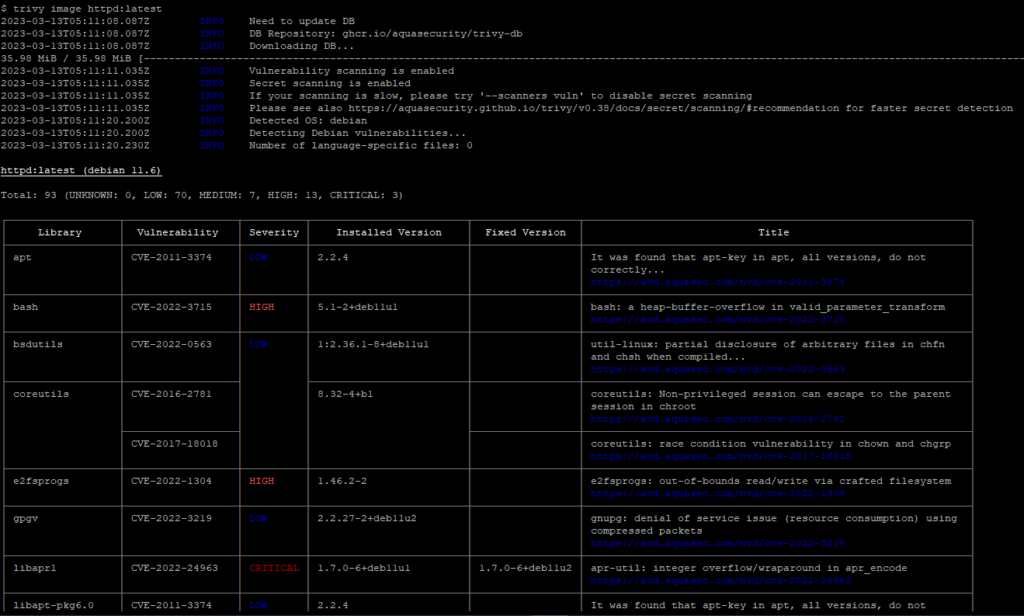
According to the report generated by Trivy, there are a total of 93 vulnerabilities in the httpd:latest image, but most of these vulnerabilities are of low severity. More attention should be paid to vulnerabilities of high and critical severity. If you want to observe vulnerabilities of a specific severity level, you can add a filter to the Trivy command.
trivy image — severity HIGH,CRITICAL httpd:latest
The report provides information such as library, vulnerability ID, severity, installed version, fixed version, and title.
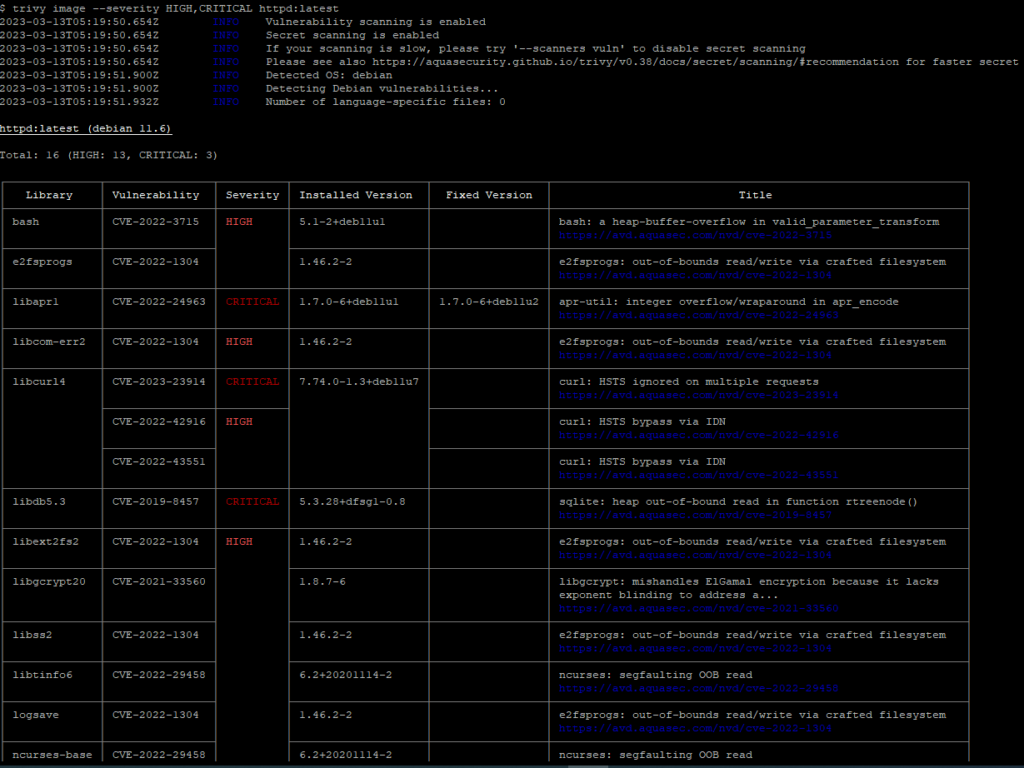
Library: Indicates which package in the container image contains a security vulnerability.
Vulnerability ID: Unique ID of the known security vulnerability. You can search for the vulnerability using this ID and examine its details.
Severity: Indicates the severity level of the vulnerability. It contains values such as high, critical, medium, and low.
Installed version: Indicates the installed version of the vulnerable package in the image.
Fixed version: Indicates the version in which the security vulnerability was patched and resolved.
Title: Provides general information about the security vulnerability.
The severity level of vulnerabilities should be taken into account, especially high and critical vulnerabilities.
To sum up, security vulnerability scanning is crucial in the container world to identify known vulnerabilities in software packages. Image scanning, a key component of DevSecOps, helps detect vulnerable packages within container images before deployment. Trivy, an open-source tool developed by Aqua Security, specializes in reporting security vulnerabilities in container images. Installation of Trivy is straightforward, with support for various operating systems. Once installed, Trivy can be used to scan images, providing a detailed report listing vulnerable packages, severity levels, installed and fixed versions, and other relevant information. Paying attention to high and critical severity vulnerabilities is essential for ensuring container security.
