Container images come with a lot of different software components. We should pay attention what is installed in the container images. We generally assume all software can include vulnerabilities that can be used by an attacker.
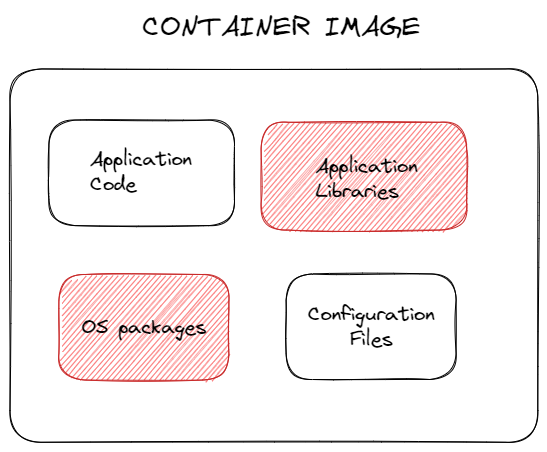
One of the best ways of minimizing base attacks is the reqularly applying the latest security patches in our container images. DevSecOps team must know the which container images they are using and what are their dependencies.
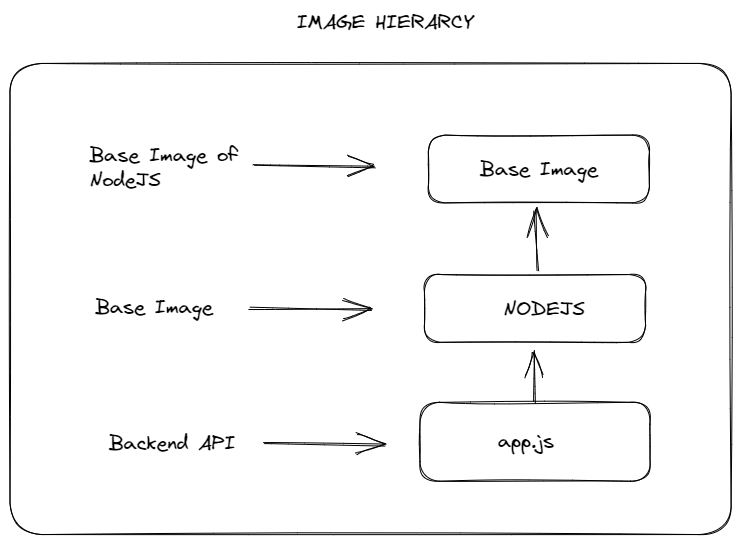
As we mentioned before, container images are build by layers. Every container images use some kind of base image. In order to create container image, you should start by defining Dockerfile which includes series of instructions how image will be built. Dockerfile usually starts from a base image. A base image is where your image is based, it is a starting point. A base image can be nginx, nodejs, mysql, ubuntu etc.
Lets assume, we have a simple backend application named customer-api, this application is build on nodejs framework so your container image should get the nodejs dependencies by using nodejs base image.
Possibly nodejs base image is built by using another base image. Base images dont just fall from the sky. They are possibly using another base image like debian, alpine, rhel, etc.
Its very critical to run secure applications in your production environment. In order to do that, you must ensure your application does not depend on vulnerable os packages and open source libraries.
You as a devsecops expert, always need to ensure that applications dont have any critical and high security vulnerabilities which attacker can use these vulnerabilities to attack your application and break your production cluster.
The most effective way is to minimize base image attack is the regularly applying security patches of base images that has critical or high security vulnerabilities. Two different methods can be followed to determine whether an image contains a security vulnerability.
Integrating image vulnerability scanning tools into the CI/CD pipeline
With this method, there is no need for manual image scanning. Devops pipeline needs to has a stage that uses image scanning tool and this must be done dynamically for each environment (test, preprod, etc.). Thus, before the product is deployed to the prod environment, critical security vulnerabilities are noticed and precautions are taken.
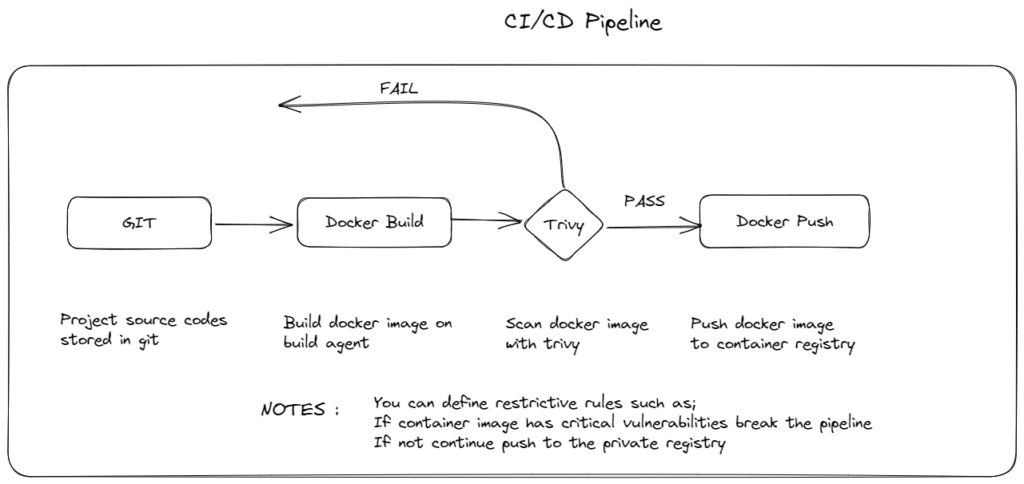
Scanning images in the image registry regularly
As the second method, a private container registry scan is performed where container images are kept. With this method, you can scan your images at set period intervals and observe whether there is a security vulnerability in the image.
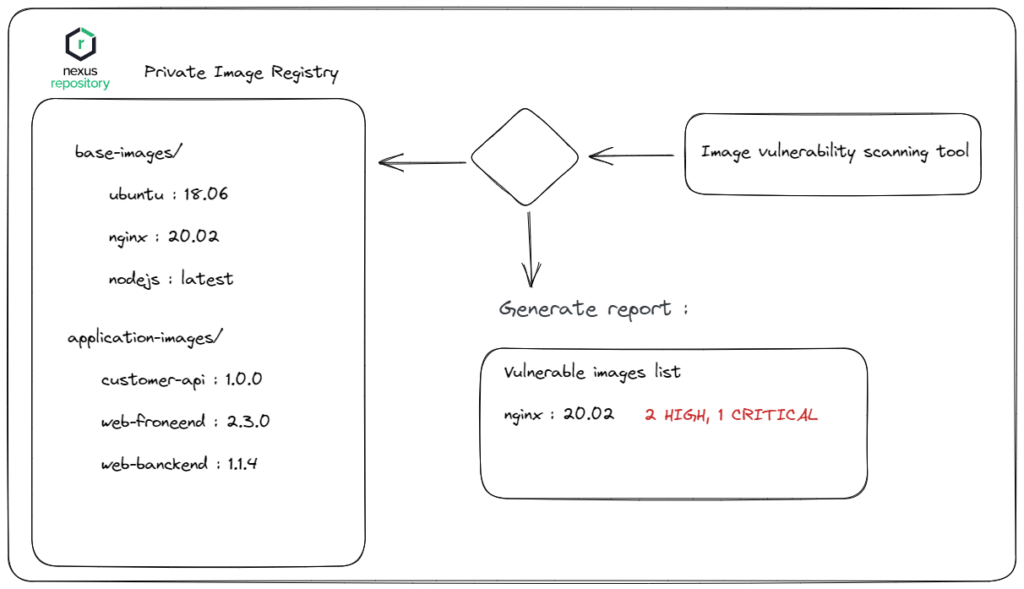
You have multiple product options to scan images. You can use trivy, which is Aquasecurity’s open source product, or you can use prismacompute. Prismacompute is paid, but besides container image scanning, it offers a few other valuable features such as runtime analysis.
You don’t have to choose one of the above two methods. Implementing both will allow you to create a safer environment. For example, if you only perform image scanning in the CI/CD pipeline, you will only evaluate security vulnerabilities for the day you scan. When you scan the images only in the pipeline, there may not be a security vulnerability in the image for that moment, but after a while, a security vulnerability may appear in a package used in the image. By using the second method to observe such situations, you will notice whether your applications running in the production environment are affected by current security vulnerabilities.
