Explore technology
September 1, 2024
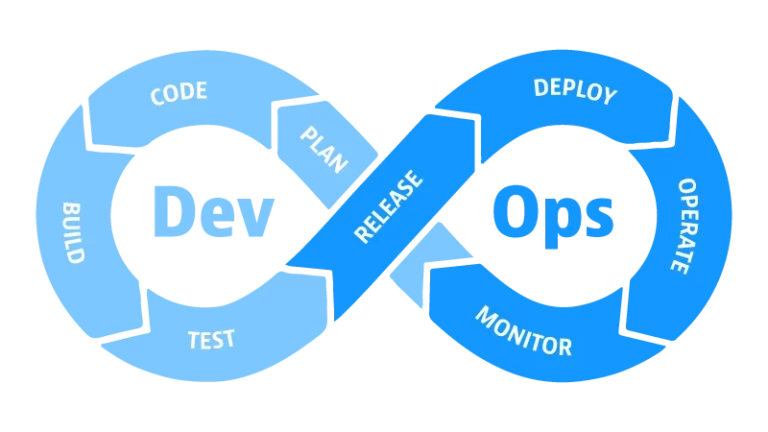
One of the main goals of DevOps culture is to automate everything as much as possible. By automating processes such as environment, application, authorization, security, quality, and testing, we establish...
April 20, 2024
One of the most important roles of DevOps practice is to automate SDLC processes as much as possible. Standard SDLC processes include transferring the developed feature to live environments and customers...
April 18, 2024
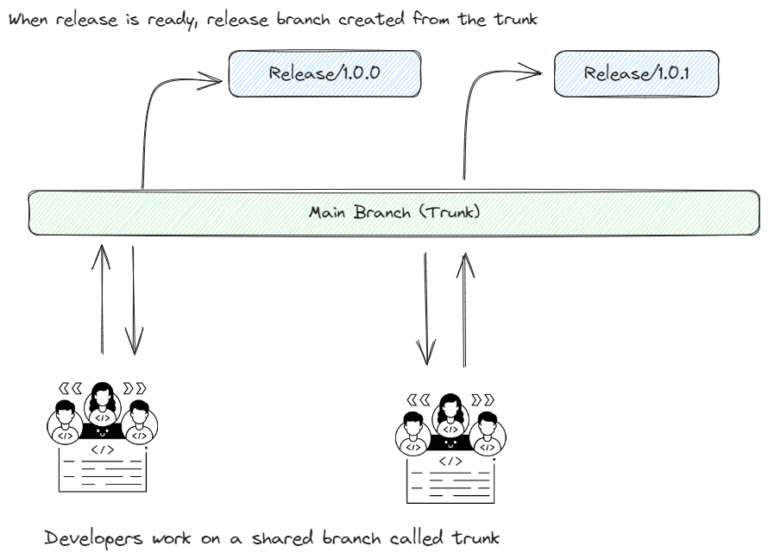
Source control management is the practice of tracking and managing changes to code. It ensures efficient collaboration within teams or across teams, as well as versioning and managing the needs of the...
April 17, 2024
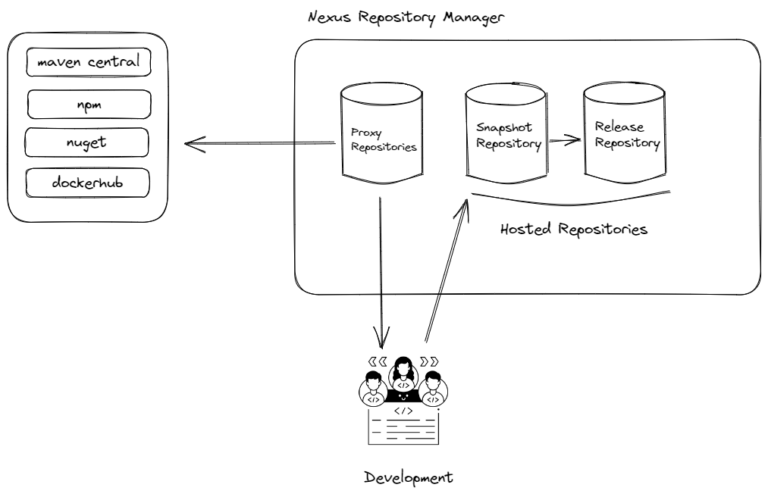
Creating and managing repositories is one of the fundamental features of Nexus Repository Manager. Understanding repository management well can facilitate the software lifecycle and assist in establishing...
April 14, 2024
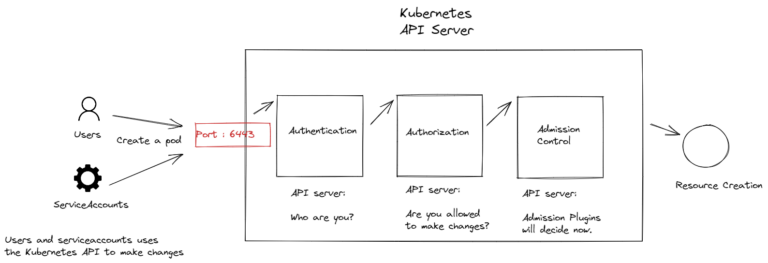
For a Devops specialist or software developer, having knowledge in Cloud native environments is an important success in your career. Having knowledge in environments such as Kubernetes will provide you...
April 13, 2024
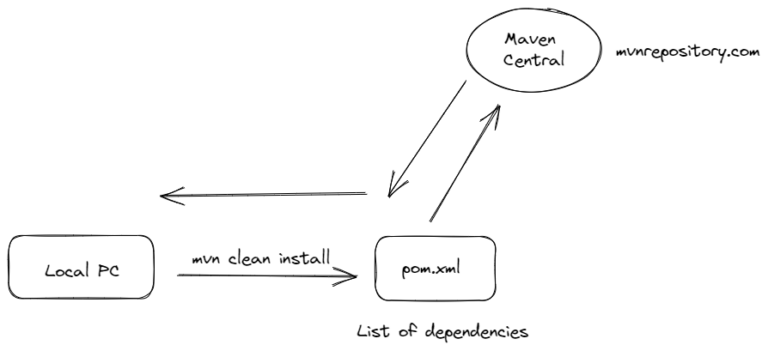
Nexus Repository Manager plays an important role in software development as it allows for proxying, collecting, distributing, and managing software dependencies.
When we look at its definition, it’s...
April 12, 2024
Logging in general is very useful for both software development and infrastructure management or security tasks. Often, when an installation is performed, the primary goal is to successfully run the installation,...
April 7, 2024
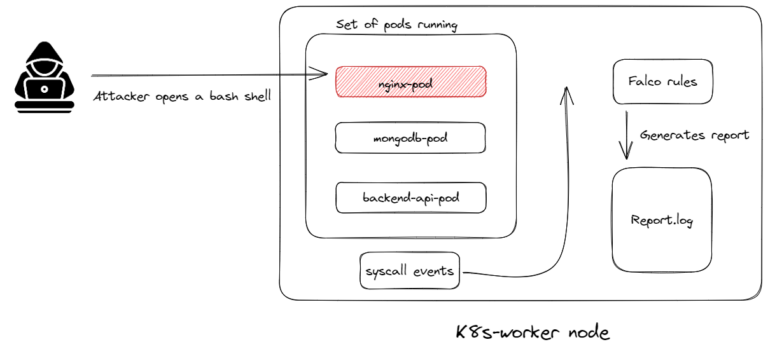
Behavioral analytics is the process of observing what is going on in a system and identifying abnormal and potentially malicious events.
If you are adopting containers and cloud, you take advantage of...
April 5, 2024
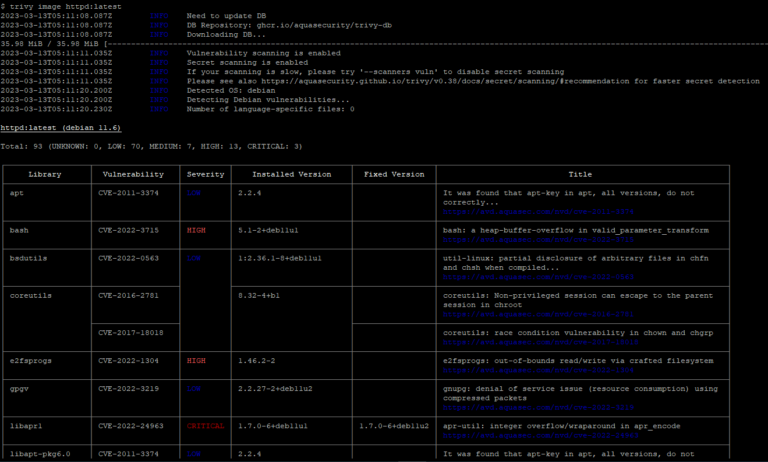
Security vulnerability scanning is a term used to identify known vulnerabilities in a software package. Just like in legacy systems, we also need to regularly perform vulnerability scans in the container...
April 5, 2024
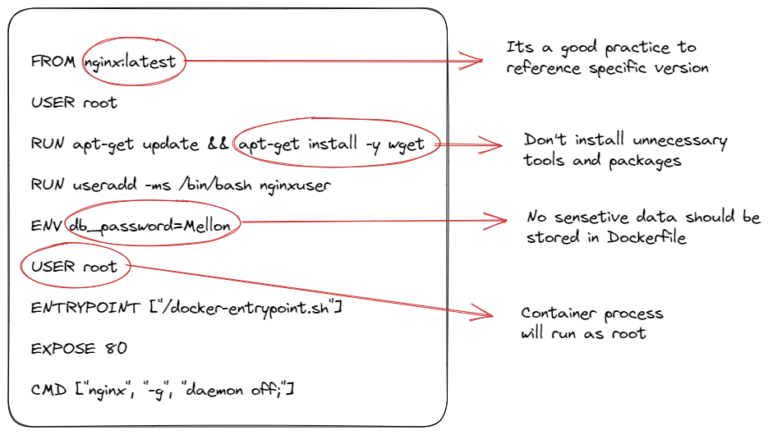
When writing Dockerfiles and Kubernetes manifests, there are some important issues to consider that will help us create a secure product and environment.In this blog post, we embark on a journey to dissect...
No posts found
1
2